# Understanding Nmap OS Detection: A Comprehensive Guide
Written on
Chapter 1: Introduction to Nmap OS Detection
Nmap is an essential tool in the arsenal of network reconnaissance and asset identification. Its OS detection feature provides a rapid and efficient method to ascertain the operating system of a remote device.
Basic Command for OS Detection
The simplest command to initiate Nmap's OS detection is as follows:
nmap -O <target>
In this command, the flag -O signifies Operating System detection, which should not be confused with the lowercase -o that is utilized for output specifications. You can replace <target> with either the hostname, like scanme.nmap.org, or an IP address, such as 45.33.32.156.
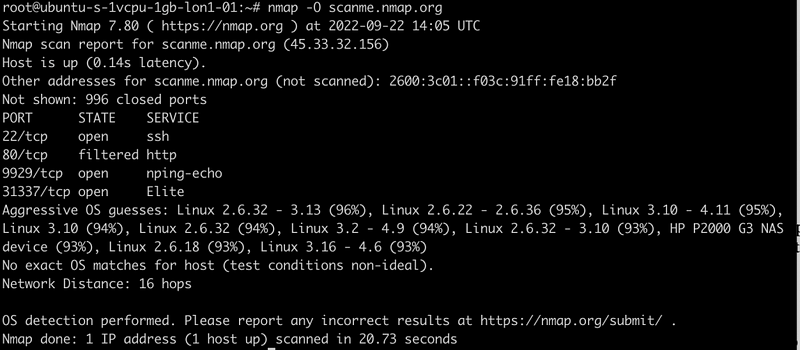
Nmap OS Detection in Practice
As illustrated in the above scan screenshot, Nmap sometimes lacks absolute certainty regarding the exact operating system of a target device. In such cases, it provides predictions accompanied by confidence levels expressed as percentages, for instance, Linux 2.6.32–3.13 (96%). Due to the nature of Nmap's OS detection, unless the device responds with its specific OS and version, this is the most precise information available. The more data Nmap gathers, the higher the accuracy of its predictions.
Section 1.1: Reducing False Positives in OS Detection
Given the inherent limitations of OS detection, a basic -O scan may yield numerous high-confidence predictions, none of which may be entirely correct. To mitigate this ambiguity and confirm the actual operating system, you can perform a more aggressive scan that includes both OS and application version detection:
nmap -A -T4 <target>
The -A flag incorporates OS detection along with application version analysis. The -T4 flag indicates an aggressive timing option (ranging from T0 for least aggressive to T5 for most aggressive). While application version detection can be time-consuming with default settings, -T4 accelerates the process. However, this level of aggressiveness may compromise stealth, so if discretion is paramount, consider using T0 or T1.
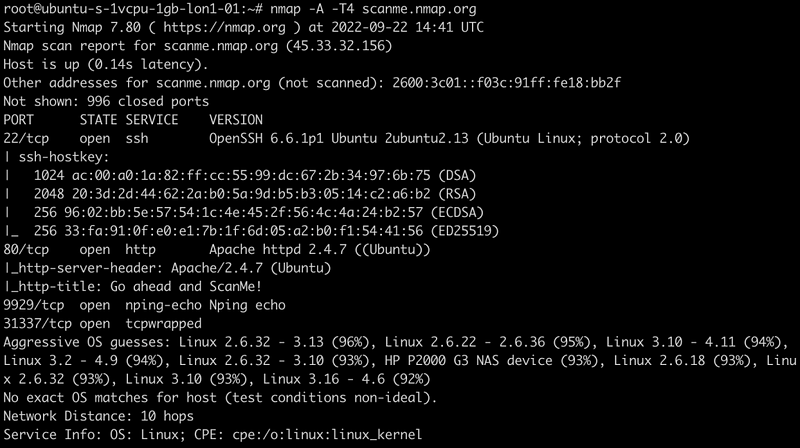
Nmap OS and Version Detection Insights
The screenshot provided above demonstrates the results of an -A -T4 scan on the same target. Unfortunately, the aggressive OS predictions remain unchanged. Fortunately, it reveals that the OpenSSH version is 2ubuntu2.13, indicating the server is operating on Ubuntu. A quick online search for "Ubuntu OpenSSH versions" suggests that the server is most likely running Ubuntu 14.04, assuming it is fully updated.
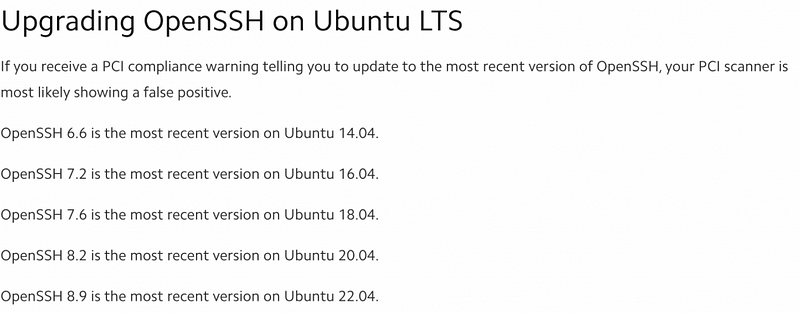
Section 1.2: Evasion Techniques for Nmap Scans
Certain firewalls and servers are configured to block ICMP ping scans, which Nmap uses to verify if a server is responsive before conducting a port scan. To bypass this limitation, you can disable the default ping check with the following command:
nmap -O -Pn <target>
The -Pn flag disables the ping check, leading Nmap to assume the host is active and proceed with the port and OS detection scan. This command can also be combined with other scan types:
nmap -Pn -A -T4 <target>
This command sequence performs an OS and application version check, bypasses ping checks, and executes the scan aggressively, sending probing messages rapidly for quicker results.
These scans can often be detected and blocked by modern, well-configured firewalls. However, many devices lack such advanced protection, and those that do are often poorly configured.
Chapter 2: Advanced Evasion Techniques
In this video, "How OS Fingerprinting Works // NMAP Tutorial," you will learn about the fundamental concepts behind OS fingerprinting and how Nmap implements these techniques.
The video "CSEP - Nmap OS Detection" further delves into advanced methods for OS detection using Nmap, showcasing practical applications and strategies.
Understanding Nmap's OS Detection Mechanism
Nmap's OS detection relies on a method known as TCP/IP Stack Fingerprinting. Although TCP/IP is a well-established standard, different operating systems implement these protocols in unique ways. Although compliant with the standard, subtle variations in how each operating system interprets ambiguities can reveal the underlying OS of a networked device.
The Nmap development team maintains an extensive database of OS and application version signatures, which is updated with each installation of Nmap. Keeping Nmap updated ensures that you have access to the latest signature updates for newly released operating systems and applications.
In essence, Nmap's OS fingerprinting process involves sending up to 16 TCP, UDP, and ICMP probes to known open and closed ports on the target machine. These specially crafted probes exploit various ambiguities in standard protocol RFCs, and Nmap listens for responses. A multitude of attributes in these responses is analyzed and synthesized to create a fingerprint.