Understanding the Complexities of Docker Networking Explained
Written on
Chapter 1: Introduction to Container Networking
If you have ever worked with Docker or containers, you are likely familiar with the challenges associated with enabling communication between them. Numerous issues and edge cases can complicate container configurations, turning what should be a straightforward task into a frustrating experience. In this article, we will delve into the reasons behind the complexities of container networking.
Section 1.1: What Are Containers?
To grasp the concept of container networking, it is essential to first understand containers themselves. In essence, containers are processes that operate in isolation, utilizing Linux cgroups and namespaces. For the purpose of this discussion, we will focus specifically on namespaces.
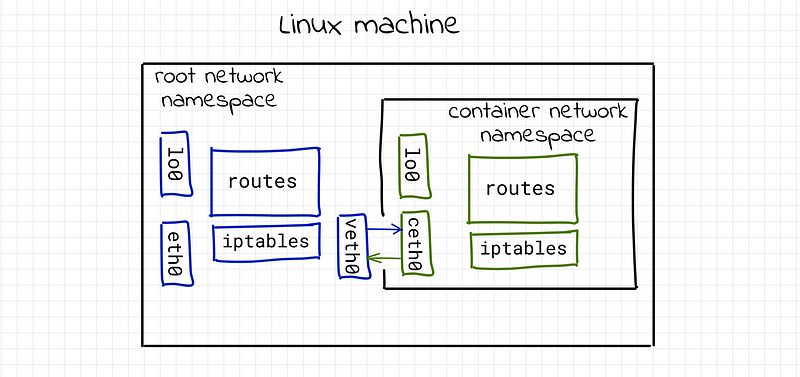
Network namespaces represent a key aspect of container architecture. By default, each container is assigned its own network namespace, complete with a unique network stack and interfaces that are separate from the host system. Each container even boasts its own IP address, typically drawn from a private IP range like 172.17.0.0/16 or 10.0.0.0/8. This setup means that containers are isolated from one another, unable to communicate with other containers, processes, or even the host itself.
Section 1.2: The Role of Network Bridges
To facilitate communication between containers on the same host, Docker provides several networking options, with the most common being the network bridge. A network bridge acts as a conduit that connects multiple networks into a larger network. When you initiate the Docker daemon on a host server, a network bridge named docker0 is automatically created.
When a container is launched, a virtual Ethernet device (veth) is generated on the host machine. One side of this veth connects to the container, while the other connects to the network bridge on the host.
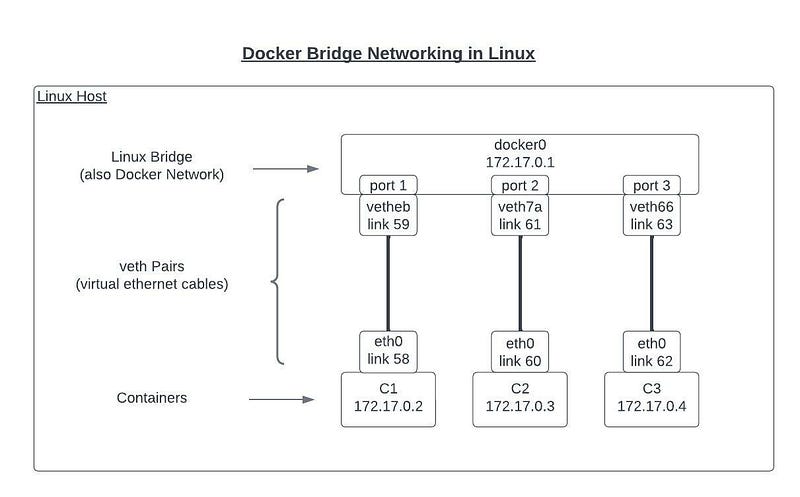
If you do not specify a custom network bridge, Docker defaults to using the docker0 bridge. However, it is advisable to create your own network, which can be easily accomplished with the command:
docker create network <network-name>
The network bridge functions like a virtual switch, allowing containers within the same network bridge to communicate seamlessly using their private IP addresses, without the need for port configurations.
Chapter 2: Exposing Containers to the Internet
One of the most significant challenges newcomers face with container networking is enabling internet access. While having distinct network namespaces prevents port conflicts (allowing multiple containers to listen on port 80), it also means that containers cannot be accessed from the host's network.
The most straightforward approach for a container to access the internet is through the host's network. To provide a container with internet access, it must be exposed to the host.
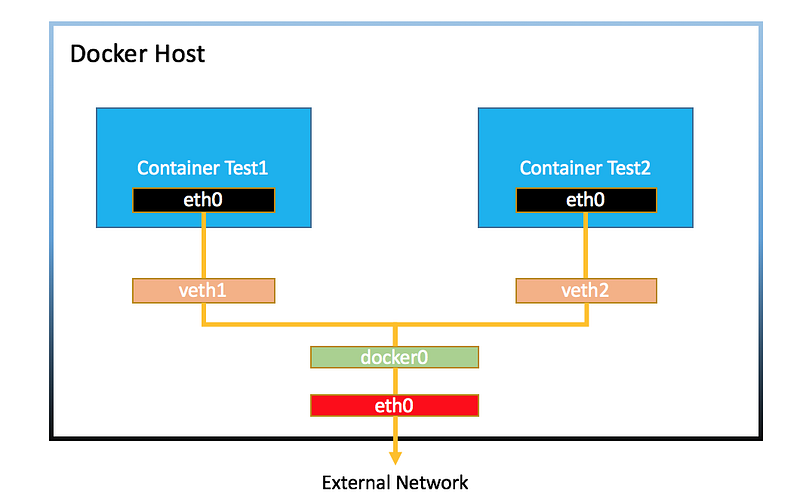
When exposing a container, you instruct the host to forward traffic to the container via a port mapping. This mapping connects the container's port to a designated public port on the host. For instance, if you have two application containers both listening on port 80, they would need to correspond to different ports on the host, such as 8080 and 8081.
Consider an example where a container with an IP address of 172.17.0.2 is set to listen on port 80. The Docker command to expose this container to the host's port 8080 would look like this:
docker run my-container -p 8080:80
This command instructs the host to direct any incoming traffic on port 8080 to port 80 of the container.
Section 2.1: How Traffic Routing Works
The underlying mechanism for this traffic routing typically involves iptables rules, which manage the redirection of traffic from the host to the container. Some examples of iptables rules that might be employed when exposing a container include:
DNAT Rule
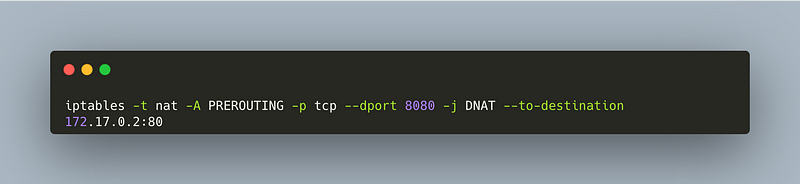
iptables -t nat -A PREROUTING -p tcp --dport 8080 -j DNAT --to-destination 172.17.0.2:80
This rule modifies the destination IP address of incoming packets, redirecting traffic intended for the host IP to the container’s IP.
MASQUERADE Rule
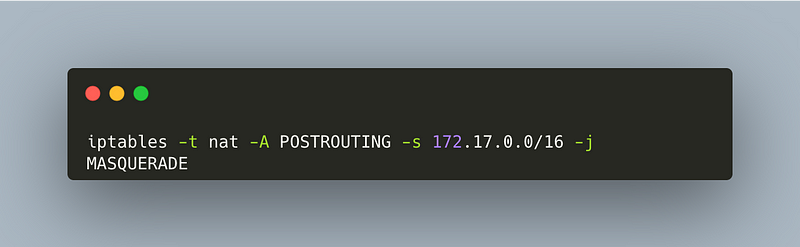
iptables -t nat -A POSTROUTING -s 172.17.0.0/16 -j MASQUERADE
This rule alters the source IP address of outbound packets, allowing containers to initiate outgoing connections while appearing to come from the host's IP address.
ACCEPT Rule
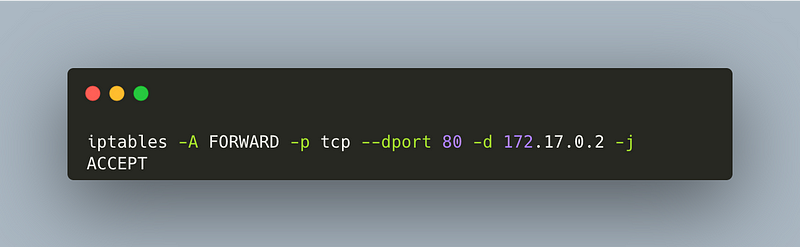
iptables -A FORWARD -p tcp --dport 80 -d 172.17.0.2 -j ACCEPT
This rule permits incoming traffic directed to the container on a specified port.
As you might imagine, managing these rules and ports can become increasingly chaotic if you are running numerous containers on a single host.
Chapter 3: Conclusion
I hope this article has provided you with valuable insights into the complexities of container networking. While you will likely encounter numerous challenges as you navigate Docker networking, understanding the foundational concepts will empower you to troubleshoot effectively when issues arise. Networking can be daunting, but mastering it is an essential skill in the world of software development.
Explore the intricacies of Docker networking in this informative video titled "Docker Networking is CRAZY!! (You NEED to learn it)" on YouTube.
Check out this comprehensive "Docker Networking Crash Course" for a deeper understanding of the topic.